The cascading effects of cyber warfare

In this publication, we will address current aspects of the cyber war being waged by the U.S. and NATO countries against Russia. Of course, the very concept of “cyber” should be understood in the traditional, Platonic sense, where “cybernet” is the ruler. Consequently, even the application of modern communication technologies is a matter of dominance and control.
On March 10, 2022 another Cyber Command legal conference was held in the US to discuss a number of legal aspects and national security issues.
Given that Russia’s operation in Ukraine was already underway by that time, the head of Cyber Command, General Nakasone, couldn’t help but mention it, noting that “Cyber Command is monitoring the digital frontline of Russian actions in Ukraine… The Russian-Ukrainian conflict increases the likelihood of Russian operations in cyberspace targeting US and allied interests… The situation in Ukraine has reinvigorated our alliances and increased the appetite for joint operations among our international partners in cyberspace. This is an open admission about the Pentagon’s elite structure working against Russia. It seems that already from the first days there have been certain conclusions in Washington.
Lieutenant General Charles Moore, who is Nakasone’s deputy, explained that combining information operations with cyber measures could give the US a strategic advantage over future adversaries. “Without a doubt, we have learned that cyber attack operations, when combined – more of a whole-of-arms approach – with what we traditionally call information operations, are an extremely powerful tool.” He said the U.S. should adopt “a strategy aimed at influencing the perceptions of adversaries.
This is a level of information-psychological, cognitive or mental warfare.
Meanwhile, Moore said the command has the authorisations needed to conduct day-to-day operations aimed at continually engaging with adversaries in cyberspace to expose their cyber measures and force them to make expenditures. “We are showing that we can operate in this space below the level of use of force – below what we would consider an armed conflict – and better defend ourselves without escalation,” he said.
To put it another way, this is the kind of hybrid warfare that NATO experts have been fond of referring to in recent years, as one of its characteristics is a level below the threshold of traditional armed conflict.
On the practical side, one must look at the NATO Locked Shields cyber exercise, which took place from 19-22 April at the Tallinn Cyber Security Centre.
According to officials, this annual real-time network defence exercise provides participants with a unique opportunity to practice protecting national civilian and military IT systems and critical infrastructure. They take place in a high-pressure environment, with a series of sophisticated cyber attacks coming at teams. The exercises are an opportunity to practice crisis cooperation between both civilian and military units, as well as the public and private sectors, as these tactical and strategic decision makers must work together in the event of a large-scale cyber attack.
In this year’s scenario, the fictional island nation of Berelia is experiencing a deteriorating security situation. A series of hostile events coincided with coordinated cyber attacks on key military and civilian IT systems.
In addition to protecting multiple cyber-physical systems, the teams involved practice tactical and strategic decision-making, cooperation and subordination in a crisis situation where they also have to deal with judicial and legal issues and respond to information operations challenges.
The similarities with Ukraine are obvious.
This year, more than 2,000 participants from 32 countries practised these actions. Some 5,500 virtualised systems were involved in the exercise, which was subjected to more than 8,000 attacks. In addition to securing complex IT systems, participating teams must also effectively report incidents and deal with forensics, legal, media operations and information warfare.
The exercise was organised by NATO in cooperation with Siemens; TalTech; Arctic Security; CR14. The Centre also recognises the unique elements added to Locked Shields 2022 by Microsoft Corporation, the Financial Services Information Sharing and Analysis Centre (FS ISAC), SpaceIT, Fortinet.
Thus we can see that large Western industry is openly assisting NATO in cyber warfare.
We should add that many Western cyber security experts and Ukrainian officials have consistently mentioned that Russia would complement its operation with a powerful cyber attack targeting critical infrastructure.
In general, military-focused publications in the U.S. continually spread information about possible new cyber attacks by Russia against critical infrastructure in the U.S. and other Western countries.
Incidentally, on the eve of the exercise, the Tallinn Center released another collective monograph on cybersecurity, devoted to attributions of cyber attacks. It accused Russia of interfering in the U.S. election and launching a cyber attack with SolarWinds in 2020.
And on 7 April, a new initiative aimed at developing critical and emerging technologies, the Defence Innovation Accelerator for the North Atlantic – DIANA, was launched at NATO headquarters.
DIANA is expected to bring defence personnel together with the Alliance’s best and brightest start-ups, academic researchers and technology companies to address critical defence and security challenges. Innovators participating in DIANA programmes will have access to a network of dozens of accelerator sites and test centres in more than 20 Allied countries. NATO leaders have agreed that DIANA will have a regional office in Europe and North America. DIANA’s European regional office was selected as a result of a joint bid by Estonia and the United Kingdom, and Canada is actively considering hosting a North American regional office.
DIANA will focus on deep and breakthrough technologies that NATO has identified as priorities, including: artificial intelligence, big data processing, quantum technologies, autonomy, biotechnology, new materials and space.
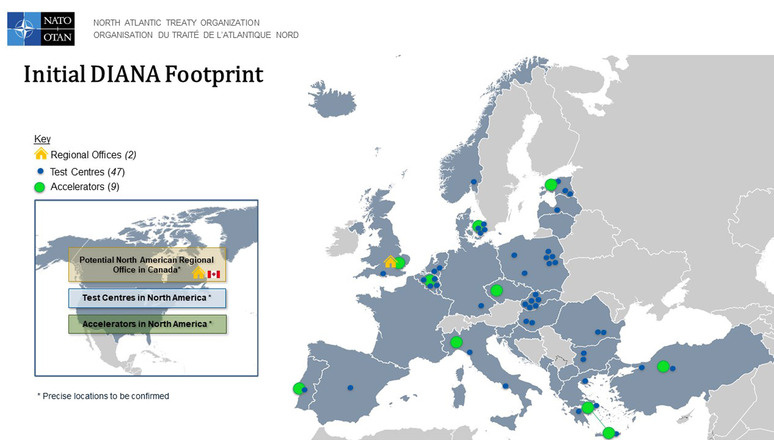
Allies also agreed to establish a NATO Multinational Innovation Fund. This is the world’s first multi-sovereign venture capital fund. It invests €1 billion in early-stage start-ups and other deep technology funds that match its strategic goals.
If you look at the map of the centres of this initiative, they are concentrated in Eastern Europe, i.e. closer to the borders of Ukraine and Russia/Belarus. This location was clearly chosen with a certain intention.
Looking at other practical aspects of waging war against Russia, the journalistic investigation into the Zignal Labs spying programme, through which the US tracked the movement of Russian troops even before the operation in Ukraine and identified the soldiers, is very important.
Obviously, this data was transmitted to the Ukrainian side.
The digitalisation of the Pentagon is also proceeding at an accelerated pace. On 25 April, one of Lyft’s executives, Craig Martell, was appointed head of digital transformation and artificial intelligence at the Pentagon.
Martell has also worked on machine learning at Dropbox and LinkedIn. It is known that his deputy will be Margaret Palmieri, head of digital warfare at the US Navy.
The US military is now using artificial intelligence to analyse combat operations in Ukraine, which allows for faster processing of large amounts of data and simulation of various scenarios. It is likely that the US wants to derive some general formula that will make it possible to calculate Russia’s vulnerabilities and use them in the future.
Moreover, judging by the U.S. State Department’s website, the agency is now focusing on anti-Russian activities, which can’t help but be alarming. If you go down to the site, you can see publications devoted exclusively to Russia in a negative light. There were three articles posted in April, although the themes are 2017, 2018 and 2020. Clearly this is built into the overall disinformation campaign against Russia. Having said that, this ShareAmerica website itself is, as indicated, made to cover life and events in the US.
Putting it all into one puzzle and adding the 24/7 flow of fabricated fakes and staging for political purposes, we get a pretty serious conclusion that needs to be reckoned with and responded to accordingly.
https://www.geopolitika.ru/en/article/cascading-effects-cyber-warfare
 TheAltWorld
TheAltWorld 
0 thoughts on “The cascading effects of cyber warfare”